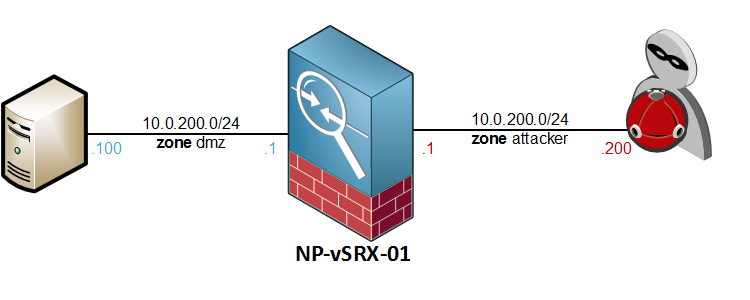
Last post in this series about Juniper Screen Options. Again, I will be working on the topology below.
OS Attacks: Ping of Death, Teardrop & WinNuke
These three are pretty old attacks, so unless you are still running some legacy system, you shouldn’t be worried about them. Anyway, here goes:
- Ping of death – This is a rather old attack in which packets were sent with a size exceeding the maximum IP datagram size of 65.535 bytes, including the headers. When reassembled, some operating systems experienced a buffer overflow, causing all sorts of unwanted behaviour. Read all about it here
- Teardrop attack – triggered by sending IP fragments with overlapping data to a remote host. When reassembling, some OS’s would crash. More information here…
- WinNuke – This is a one-packet-kill attack, which was performed by sending a NetBIOS packet with Out-of-Band data. Windows 95 could not handle this and would possibly BSOD. Used in abundance on IRC in the days 🙂 More info here
Enabling these screens is just a matter of turning on the switch:
[edit security screen ids-option Attack-Screen] root@NP-vSRX-01# set tcp winnuke [edit security screen ids-option Attack-Screen] root@NP-vSRX-01# set ip tear-drop [edit security screen ids-option Attack-Screen] root@NP-vSRX-01# set icmp ping-death
By enabling it, JunOS will look for the typical attack signatures in the packets and when detected, filter it. It’s not a bad idea to leave it enabled. Who knows, you might find someone still trying the WinNuke attack against your Windows 2012 servers 🙂
I don’t have any prehistoric OS’es lying around so I can’t test these ones.
unknown-protocol – Blocking packets with invalid protocol numbers
Although your security policy will probably be allowing only TCP, UDP and perhaps some traffic related to VPNs or routing protocols, this screen will check the packets for invalid (non-assigned) IP protocols before they enter the traffic flow. IANA has a list with all the protocol number assignments. Any protocol number not on the list should be dropped by JunOS. Wonder if Juniper keeps the software updated when new numbers are allocated.
Enabling the screen is again straight-forward:
[edit security screen ids-option Attack-Screen] root@NP-vSRX-01# set ip bad-option
syn-frag – Fragmented SYN packets
SYN packets are always very minimal in size, so it’s abnormal to have a SYN packet with the Fragment bit set. Junos will block this type of packet upon arrival on the interface.
[edit security screen ids-option Attack-Screen] root@NP-vSRX-01# set tcp syn-frag
By configuring nping to set the SYN-flag and the More Fragments bit we can craft a syn-frag packet
lab@Host200:~$ sudo nping --tcp --flags SYN 10.0.100.100 -p 21 --mf Starting Nping 0.6.46 ( http://nmap.org/nping ) at 2015-08-16 20:36 CEST SENT (0.0025s) TCP 10.0.200.200:15585 > 10.0.100.100:21 S ttl=64 id=52614 iplen=40 frag offset=0+ seq=3992461002 win=1480 SENT (1.0027s) TCP 10.0.200.200:15585 > 10.0.100.100:21 S ttl=64 id=52614 iplen=40 frag offset=0+ seq=3992461002 win=1480 SENT (2.0040s) TCP 10.0.200.200:15585 > 10.0.100.100:21 S ttl=64 id=52614 iplen=40 frag offset=0+ seq=3992461002 win=1480 SENT (3.0053s) TCP 10.0.200.200:15585 > 10.0.100.100:21 S ttl=64 id=52614 iplen=40 frag offset=0+ seq=3992461002 win=1480 SENT (4.0066s) TCP 10.0.200.200:15585 > 10.0.100.100:21 S ttl=64 id=52614 iplen=40 frag offset=0+ seq=3992461002 win=1480 Max rtt: N/A | Min rtt: N/A | Avg rtt: N/A Raw packets sent: 5 (200B) | Rcvd: 0 (0B) | Lost: 5 (100.00%) Nping done: 1 IP address pinged in 5.01 seconds
And again, the SRX performed as expected:
2015-08-16 18:31:22 UTC SYN fragment! source: 10.0.200.200:53479, destination: 10.0.100.100:21, zone name: attacker, interface name: ge-0/0/2.0, action: drop
Configuring the aggressive session ageout option
Another way to keep your firewalls session table from getting clogged is to configure an aggressive session timeout, also known as early aging. This will cause the SRX to age out idle sessions significantly faster than the default values (e.g. 30 minutes for TCP). All you need to do is define a low and high watermark, which is a percentage of the total sessions your box can handle, and a new “aggressive” age-out timer.
You can find out how much your SRX supports by entering the show security monitoring fpc 0 command (more FPCs are possible depending on model) and observing the Max flow session field. For example, the vSRX supports a total of 262144 sessions.
root@NP-vSRX-01> show security monitoring fpc 0
FPC 0
PIC 0
CPU utilization : 0 %
Memory utilization : 63 %
Current flow session : 3
Current flow session IPv4: 3
Current flow session IPv6: 0
Max flow session : 262144
Total Session Creation Per Second (for last 96 seconds on average): 0
IPv4 Session Creation Per Second (for last 96 seconds on average): 0
IPv6 Session Creation Per Second (for last 96 seconds on average): 0
There are three values to consider when configuring the feature:
high-watermark – This is the percentage of total session capacity that should be reached before the mechanism kicks in. Suppose that we define a high watermark of 75 percent on this vSRX, then it will start applying the aggressive timer once it reaches 196608 (=262144*0.75) sessions.
low-watermark – The percentage of session capacity it should reach to disable aggressive aging and go back to the default session timeout.
early-ageout – Agressive timeout period, in seconds.
Suppose that we want the vSRX to start agressively shutting down sessions that have been idle for more than 30 seconds once it is at 75 percent of its capacity, and resume normal operations when it hits 50 percent again, we would go to the security flow branch and configure the following:
[edit security flow]
root@NP-vSRX-01# show
aging {
early-ageout 30;
low-watermark 50;
high-watermark 75;
}
Monitoring Screen Options
A couple of commands that will help monitor the alarms and configuration
show configuration security screen – Shows the syntax in the config file
root@NP-vSRX-01> show configuration security screen
ids-option Attack-Screen {
description "Screen Attacker Zone";
icmp {
ip-sweep;
}
ip {
bad-option;
record-route-option;
timestamp-option;
security-option;
stream-option;
spoofing;
source-route-option;
loose-source-route-option;
strict-source-route-option;
}
tcp {
syn-fin;
fin-no-ack;
tcp-no-flag;
syn-frag;
port-scan threshold 3000;
syn-ack-ack-proxy threshold 4;
land;
}
}
show security screen ids-option [screen-name] – shows the enabled screens in a more readable format
root@NP-vSRX-01> show security screen ids-option Attack-Screen Description: Screen Attacker Zone Screen object status: Name Value TCP port scan threshold 3000 ICMP address sweep threshold 5000 IP spoofing enabled IP source route option enabled TCP land attack enabled TCP SYN fragment enabled TCP no flag enabled IP bad options enabled IP record route option enabled IP timestamp option enabled IP security option enabled IP loose source route option enabled IP strict source route option enabled IP stream option enabled TCP SYN FIN enabled TCP FIN no ACK enabled TCP SYN-ACK-ACK proxy threshold 4
show security zones [zone-name] – Shows you which screen is applied to a particular zone
root@NP-vSRX-01> show security zones attacker
Security zone: attacker
Send reset for non-SYN session TCP packets: Off
Policy configurable: Yes
Screen: Attack-Screen
Interfaces bound: 1
Interfaces:
ge-0/0/2.0
show security screen statistics zone [zone-name] – shows you the hitcount for all the screens.
root@NP-vSRX-01> show security screen statistics zone attacker Screen statistics: IDS attack type Statistics ICMP flood 0 UDP flood 0 TCP winnuke 0 TCP port scan 47 UDP port scan 0 ICMP address sweep 0 TCP sweep 0 UDP sweep 0 IP tear drop 0 TCP SYN flood 0 IP spoofing 0 ICMP ping of death 0 IP source route option 0 TCP land attack 0 TCP SYN fragment 13 TCP no flag 791118 IP unknown protocol 0 IP bad options 0 IP record route option 0 IP timestamp option 0 IP security option 0 IP loose source route option 0 IP strict source route option 0 IP stream option 0 ICMP fragment 0 ICMP large packet 0 TCP SYN FIN 20 TCP FIN no ACK 20 Source session limit 0 TCP SYN-ACK-ACK proxy 0 IP block fragment 0 Destination session limit 0 IPv6 extension header 0 IPv6 extension hop by hop option 0 IPv6 extension destination option 0 IPv6 extension header limit 0 IPv6 malformed header 0 ICMPv6 malformed packet 0
show security log – Shows you the syslog events with a bit more detail. Best to send this to a syslog server for retention…
2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:58501, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:58502, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:58503, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:58504, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:58505, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:7343, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:7344, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:7345, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:7346, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:7347, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:7348, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:7349, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:7350, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:7351, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:7352, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop 2015-08-16 18:45:31 UTC No TCP flag! source: 10.0.200.200:7353, destination: 10.0.100.100:0, zone name: attacker, interface name: ge-0/0/2.0, action: drop
Wrapping up
This was my last post on the Screen Options. I have omitted a few from the JNCIS-SEC study guide, either because I see little use for them in production or because there’s little to do in the lab besides turning it on.
Frankly, I never bothered with Screen Options because I wasn’t all familiar with them but I really see the benefits of having many of them enabled.
Anyway, if you’ve made it through the posts, thanks for reading and feel free to add a comment. Next labs, all about NAT 🙂