In this NAT configuration example I will be configuring Interface Network Adress Translation on the Juniper SRX, which will translate the source address of the original packets to the external interface addresss of the SRX.
This is the topology I will be using for all NAT configurations.
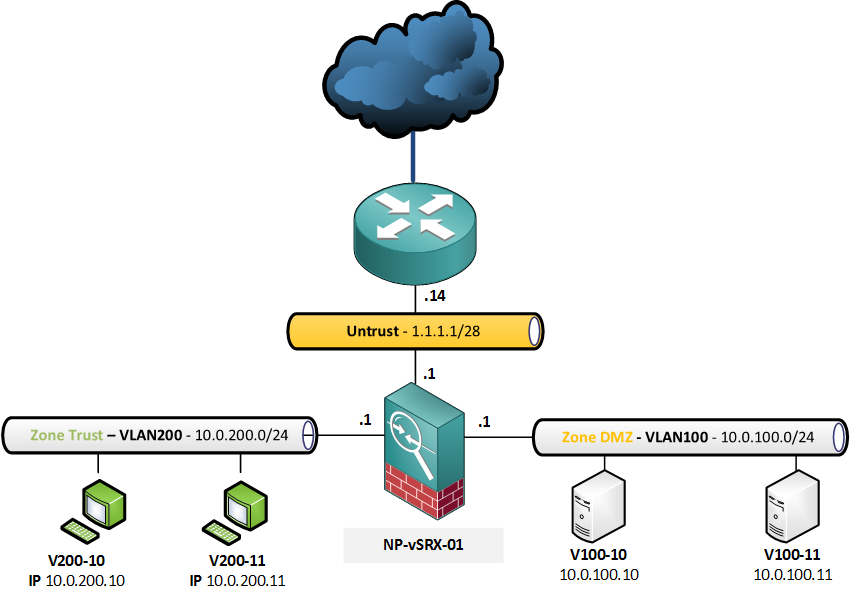
These are the requirements for the configuration:
- Traffic from the hosts in range 10.0.200.0/24
- Destined to the untrust zone (the internet)
- will be SNAT’ed to external interface IP of 1.1.1.1/32
First, I will configure an address book object for the network range.
[edit security zones security-zone trust] root@NP-vSRX-01# set address-book address Net-10.0.200.0-24 10.0.200.0/24
And configure a security policy that allows http, https and dns-udp to the internet (any).
[edit security policies from-zone trust to-zone untrust policy FW-PermitWeb]
root@NP-vSRX-01# show
match {
source-address Net-10.0.200.0-24;
destination-address any;
application [ junos-http junos-https junos-dns-udp ];
}
then {
permit;
log {
session-close;
}
}
To define the source NAT, I will first create a rule set that is specific for this zone pair.
Note – Rule-sets are where you will group different NAT rules based on traffic direction. You can match on interface, zone and routing-instance, as displayed below. When two rule-sets match for a particular traffic flow, the most specific one will be preferred, with interface being the most specific, then zones and finally routing-instances.
[edit security nat source rule-set NAT-Trust-to-Internet] root@NP-vSRX-01# set from ? Possible completions: + interface Source interface list + routing-instance Source routing instance list + zone Source zone list
The rule-set for this zone pair:
[edit security nat source]
root@NP-vSRX-01# show
rule-set NAT-Trust-to-Internet {
from zone trust;
to zone untrust;
}
And here is the NAT rule I have defined:
[edit security nat source rule-set NAT-Trust-to-Internet]
root@NP-vSRX-01# show rule NAT-Source-VLAN200
match {
source-address 10.0.200.0/24;
}
then {
source-nat {
interface;
}
}
I could have also defined to match on 0.0.0.0/0 as the destination address, but that would just have been one more line of code.
Verifiying the translations:
root@NP-vSRX-01> show security flow session source-prefix 10.0.200.0/24 Session ID: 17713, Policy name: FW-PermitWeb/4, Timeout: 2, Valid In: 10.0.200.10/49751 --> 8.8.8.8/53;udp, If: ge-0/0/2.0, Pkts: 1, Bytes: 55 Out: 8.8.8.8/53 --> 1.1.1.1/29242;udp, If: ge-0/0/0.0, Pkts: 1, Bytes: 71 Session ID: 17714, Policy name: FW-PermitWeb/4, Timeout: 2, Valid In: 10.0.200.10/49751 --> 8.8.4.4/53;udp, If: ge-0/0/2.0, Pkts: 1, Bytes: 55 Out: 8.8.4.4/53 --> 1.1.1.1/13555;udp, If: ge-0/0/0.0, Pkts: 1, Bytes: 71 Total sessions: 2
We see an internal traffic flow from 10.0.200.10 going to 8.8.8.8 and 8.8.4.4 (IN). The return traffic (OUT) is being sent to a translated port on 1.1.1.1, the interface IP.
This means that the NAT is working as required.
For a brief summary of the NAT configuration, enter the following:
root@NP-vSRX-01> show security nat source summary Total port number usage for port translation pool: 0 Maximum port number for port translation pool: 33554432 Total pools: 0 Total rules: 1 Rule name Rule set From To Action NAT-Source-VLAN200 NAT-Trust-to-Internet trust untrust interface
And to view even more detail and some statistics about the rule:
root@NP-vSRX-01> show security nat source rule NAT-Source-VLAN200
source NAT rule: NAT-Source-VLAN200 Rule-set: NAT-Trust-to-Internet
Rule-Id : 1
Rule position : 1
From zone : trust
To zone : untrust
Match
Source addresses : 10.0.200.0 - 10.0.200.255
Action : interface
Persistent NAT type : N/A
Persistent NAT mapping type : address-port-mapping
Inactivity timeout : 0
Max session number : 0
Translation hits : 604
Successful sessions : 604
Failed sessions : 0
Number of sessions : 0
One thought on “JNCIS-SEC Lab – Interface NAT on the SRX”