In the previous article, I configured the SRX to translate outgoing traffic to the external interface IP. In this article, we will look at a second way of configuring Source NAT, using a NAT address pool.
Again, I will be using the same topology:
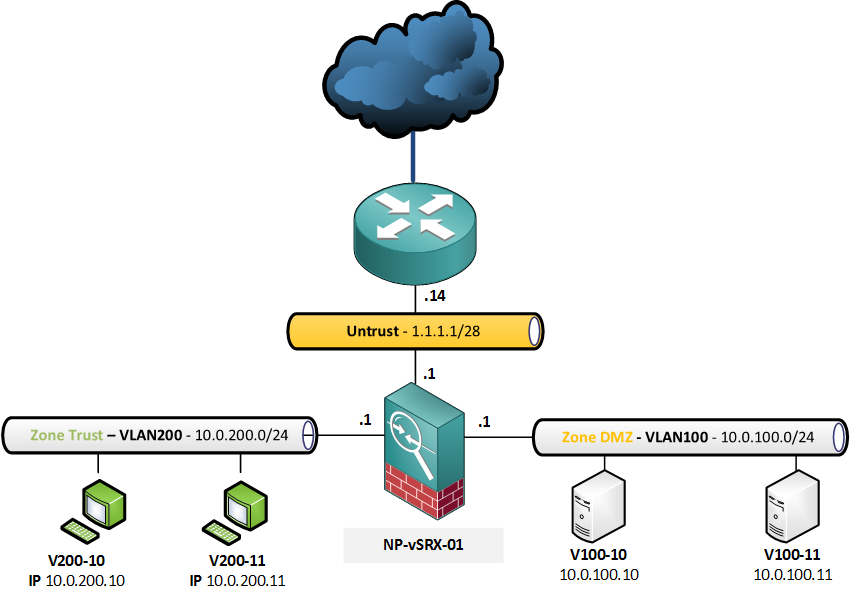
For the Source NAT with address pool, this is the requirement:
- Traffic from the hosts in range 10.0.200.0/24
- Destined to the untrust zone (the internet)
- will be SNAT’ed to a pool with one IP address, 1.1.1.2/32
The firewall policies from the previous article, which allow basic web access, are still in place:
root@NP-vSRX-01# show security policies from-zone trust to-zone untrust
policy FW-PermitWeb {
match {
source-address Net-10.0.200.0-24;
destination-address any;
application [ junos-http junos-https junos-dns-udp ];
}
then {
permit;
log {
session-close;
}
}
}
First, configure a rule-set that defines the traffic direction:
[edit security nat source]
root@NP-vSRX-01# show
rule-set NAT-Trust-to-Internet {
from zone trust;
to zone untrust;
}
Then, create the address pool:
[edit security nat source]
root@NP-vSRX-01# set pool SNAT-Pool-Trust-to-Internet address 1.1.1.2/32
Next, configure the NAT rule based on the requirements:
[edit security nat source rule-set NAT-Trust-to-Internet rule NAT-Source-VLAN200]
root@NP-vSRX-01# show
match {
source-address 10.0.200.0/24;
}
then {
source-nat {
pool {
SNAT-Pool-Trust-to-Internet;
}
}
}
After a commit, the SRX is correctly translating the traffic to 1.1.1.2 (Out > In traffic):
root@NP-vSRX-01> show security flow session source-prefix 10.0.200.10/32
Session ID: 38803, Policy name: FW-PermitWeb/4, Timeout: 42, Valid
In: 10.0.200.10/23772 --> 8.8.8.8/53;udp, If: ge-0/0/2.0, Pkts: 1, Bytes: 63
Out: 8.8.8.8/53 --> 1.1.1.2/15049;udp, If: ge-0/0/0.0, Pkts: 0, Bytes: 0
### omitted for brevity ###
Session ID: 38809, Policy name: FW-PermitWeb/4, Timeout: 42, Valid
In: 10.0.200.10/15346 --> 8.8.8.8/53;udp, If: ge-0/0/2.0, Pkts: 1, Bytes: 67
Out: 8.8.8.8/53 --> 1.1.1.2/13144;udp, If: ge-0/0/0.0, Pkts: 0, Bytes: 0
Total sessions: 7
Unfortunately, the machine does not have internet access yet. As we are translating to an address other than our interface IP, the upstream router does not have an ARP entry for it. To solve this problem, we could add a static route on the “ISP” router, or configure Proxy-ARP on the SRX. In the real world, getting an ISP to make changes would take days so let’s do Proxy ARP.
First, find the interface which has our public IP:
[edit security nat]
root@NP-vSRX-01# run show interfaces terse | match 1.1.1.1
ge-0/0/0.0 up up inet 1.1.1.1/28
Then, configure the proxy-arp as a global NAT command:
[edit security nat]
root@NP-vSRX-01# set proxy-arp interface ge-0/0/0.0 address 1.1.1.2
Let’s see if we now have more sessions from the clients:
root@NP-vSRX-01# run show security flow session source-prefix 10.0.200.0/24
Session ID: 38967, Policy name: FW-PermitWeb/4, Timeout: 1792, Valid
In: 10.0.200.10/54278 --> 54.149.61.73/443;tcp, If: ge-0/0/2.0, Pkts: 10, Bytes: 1265
Out: 54.149.61.73/443 --> 1.1.1.2/4408;tcp, If: ge-0/0/0.0, Pkts: 8, Bytes: 3905
Session ID: 38971, Policy name: FW-PermitWeb/4, Timeout: 292, Valid
In: 10.0.200.10/52289 --> 91.189.89.88/80;tcp, If: ge-0/0/2.0, Pkts: 7, Bytes: 1145
Out: 91.189.89.88/80 --> 1.1.1.2/29288;tcp, If: ge-0/0/0.0, Pkts: 5, Bytes: 952
Session ID: 38975, Policy name: FW-PermitWeb/4, Timeout: 298, Valid
In: 10.0.200.10/42145 --> 93.184.220.29/80;tcp, If: ge-0/0/2.0, Pkts: 7, Bytes: 1250
Out: 93.184.220.29/80 --> 1.1.1.2/24688;tcp, If: ge-0/0/0.0, Pkts: 5, Bytes: 1844
Session ID: 38986, Policy name: FW-PermitWeb/4, Timeout: 1792, Valid
In: 10.0.200.10/39442 --> 68.232.34.191/443;tcp, If: ge-0/0/2.0, Pkts: 9, Bytes: 1144
Out: 68.232.34.191/443 --> 1.1.1.2/5689;tcp, If: ge-0/0/0.0, Pkts: 16, Bytes: 14208
### omitted for brevity ###
Session ID: 39167, Policy name: FW-PermitWeb/4, Timeout: 1792, Valid
In: 10.0.200.10/42964 --> 37.252.170.5/443;tcp, If: ge-0/0/2.0, Pkts: 7, Bytes: 1577
Out: 37.252.170.5/443 --> 1.1.1.2/6620;tcp, If: ge-0/0/0.0, Pkts: 6, Bytes: 1515
Session ID: 39169, Policy name: FW-PermitWeb/4, Timeout: 1792, Valid
In: 10.0.200.10/42966 --> 37.252.170.5/443;tcp, If: ge-0/0/2.0, Pkts: 8, Bytes: 1641
Out: 37.252.170.5/443 --> 1.1.1.2/25579;tcp, If: ge-0/0/0.0, Pkts: 7, Bytes: 1636
Session ID: 39172, Policy name: FW-PermitWeb/4, Timeout: 1794, Valid
In: 10.0.200.10/45036 --> 37.252.170.182/443;tcp, If: ge-0/0/2.0, Pkts: 11, Bytes: 3599
Out: 37.252.170.182/443 --> 1.1.1.2/32160;tcp, If: ge-0/0/0.0, Pkts: 10, Bytes: 6143
Total sessions: 55
Now that it’s working and we have HTTP and HTTPS sessions established, here is the full configuration again:
[edit security nat]
root@NP-vSRX-01# show
source {
pool SNAT-Pool-Trust-to-Internet {
address {
1.1.1.2/32;
}
}
rule-set NAT-Trust-to-Internet {
from zone trust;
to zone untrust;
rule NAT-Source-VLAN200 {
match {
source-address 10.0.200.0/24;
}
then {
source-nat {
pool {
SNAT-Pool-Trust-to-Internet;
}
}
}
}
}
}
proxy-arp {
interface ge-0/0/0.0 {
address {
1.1.1.2/32;
}
}
}
Translating to a range, with PAT
When using Port Address Translation, using one IP address gives us a theoretical 65.536 available ports (less are used for outbound connections), which means an equal amount of concurrent sessions. When we are nearing the limit with one IP address, we can add more addresses to the pool.
Suppose that we want to add 1.1.1.3/32 to the mix, we have two options. We can change the mask to /31:
[edit security nat source pool SNAT-Pool-Trust-to-Internet]
root@NP-vSRX-01# show
address {
1.1.1.2/31;
}
Or, we can specify a from-to range:
[edit security nat source pool SNAT-Pool-Trust-to-Internet]
root@NP-vSRX-01# show
address {
1.1.1.2/32 to 1.1.1.3/32;
}
After a commit, the flow table shows it’s translating to both 1.1.1.2 and 1.1.1.3 for one of my lab machines:
[edit security nat source pool SNAT-Pool-Trust-to-Internet]
root@NP-vSRX-01# run show security flow session
Session ID: 123095, Policy name: FW-PermitWeb/4, Timeout: 52, Valid
In: 10.0.200.11/10224 --> 8.8.8.8/53;udp, If: ge-0/0/2.0, Pkts: 3, Bytes: 189
Out: 8.8.8.8/53 --> 1.1.1.3/15041;udp, If: ge-0/0/0.0, Pkts: 0, Bytes: 0
### omitted ###
Session ID: 123104, Policy name: FW-PermitWeb/4, Timeout: 2, Valid
In: 10.0.200.11/24055 --> 8.8.8.8/53;udp, If: ge-0/0/2.0, Pkts: 1, Bytes: 67
Out: 8.8.8.8/53 --> 1.1.1.2/26041;udp, If: ge-0/0/0.0, Pkts: 1, Bytes: 179
Session ID: 123105, Policy name: FW-PermitWeb/4, Timeout: 58, Valid
In: 10.0.200.11/57407 --> 8.8.8.8/53;udp, If: ge-0/0/2.0, Pkts: 1, Bytes: 65
Out: 8.8.8.8/53 --> 1.1.1.3/2018;udp, If: ge-0/0/0.0, Pkts: 0, Bytes: 0
Session ID: 123106, Policy name: FW-PermitWeb/4, Timeout: 2, Valid
In: 10.0.200.11/46570 --> 8.8.8.8/53;udp, If: ge-0/0/2.0, Pkts: 1, Bytes: 67
Out: 8.8.8.8/53 --> 1.1.1.2/11394;udp, If: ge-0/0/0.0, Pkts: 1, Bytes: 123
Session ID: 123107, Policy name: FW-PermitWeb/4, Timeout: 18, Valid
In: 10.0.200.11/33438 --> 91.189.92.201/80;tcp, If: ge-0/0/2.0, Pkts: 2, Bytes: 120
Out: 91.189.92.201/80 --> 1.1.1.3/17036;tcp, If: ge-0/0/0.0, Pkts: 0, Bytes: 0
Total sessions: 9
Unfortunately, this doesn’t always work flawlessly. We can instruct JunOS to always NAT one particular client to the same external IP by adding the global source-NAT command address-persistent
[edit security nat source]
root@NP-vSRX-01# set address-persistent
[edit security nat source]
root@NP-vSRX-01# commit
commit complete
Disabling Port Address Translation
By default, the SRX will translate the outgoing port to a random number. We can disable this by adding port no-translation to the pool configuration.
Assume the following configuration:
- The previous SNAT pool of 1.1.1.2/31 will remain as configured but PAT will be disabled
- If the SRX runs out of available ports, we will PAT to the interface IP. This is referred to as an overflow pool.
SourceNAT configuration:
[edit security nat source pool SNAT-Pool-Trust-to-Internet]
root@NP-vSRX-01# show
address {
1.1.1.2/32 to 1.1.1.3/32;
}
port {
no-translation;
}
overflow-pool interface;
As shown below, the outgoing port stays the same on both the ingress and egress session.
oot@NP-vSRX-01# run show security flow session
Session ID: 164827, Policy name: FW-PermitWeb/4, Timeout: 290, Valid
In: 10.0.200.10/48125 --> 91.189.91.23/80;tcp, If: ge-0/0/2.0, Pkts: 25, Bytes: 5621
Out: 91.189.91.23/80 --> 1.1.1.2/48125;tcp, If: ge-0/0/0.0, Pkts: 24, Bytes: 5768[edit]
To conclude, here are some show commands that will help during config and troubleshooting
root@NP-vSRX-01> show security nat source summary
Total port number usage for port translation pool: 64512
Maximum port number for port translation pool: 33554432
Total pools: 1
Pool Address Routing PAT Total
Name Range Instance Address
SNAT-Pool-Trust-to-Internet 1.1.1.2-1.1.1.2 default yes 1
Total rules: 1
Rule name Rule set From To Action
NAT-Source-VLAN200 NAT-Trust-to-Internet trust untrust SNAT-Pool-Trust-to-Internet
root@NP-vSRX-01> show security nat source pool SNAT-Pool-Trust-to-Internet
Pool name : SNAT-Pool-Trust-to-Internet
Pool id : 4
Routing instance : default
Host address base : 0.0.0.0
Port : [1024, 63487]
Twin port : [63488, 65535]
Port overloading : 1
Address assignment : no-paired
Total addresses : 1
Translation hits : 275
Address range Single Ports Twin Ports
1.1.1.2 - 1.1.1.2 1 0
root@NP-vSRX-01> show security nat source rule all
Total rules: 1
Total referenced IPv4/IPv6 ip-prefixes: 1/0
source NAT rule: NAT-Source-VLAN200 Rule-set: NAT-Trust-to-Internet
Rule-Id : 1
Rule position : 1
From zone : trust
To zone : untrust
Match
Source addresses : 10.0.200.0 - 10.0.200.255
Action : SNAT-Pool-Trust-to-Internet
Persistent NAT type : N/A
Persistent NAT mapping type : address-port-mapping
Inactivity timeout : 0
Max session number : 0
Translation hits : 275
Successful sessions : 275
Failed sessions : 0
Number of sessions : 1
