I already went into source and destination NAT in the last few posts. The last one I wanted to lab up is Static NAT, which creates a one-to-one mapping between two addresses. The translation is bidirectional and ports are not translated. On the downside, it does require you to sacrifice one public IP per internal server which is not always the most cost-efficient method.
Here’s what I’ll be working on:
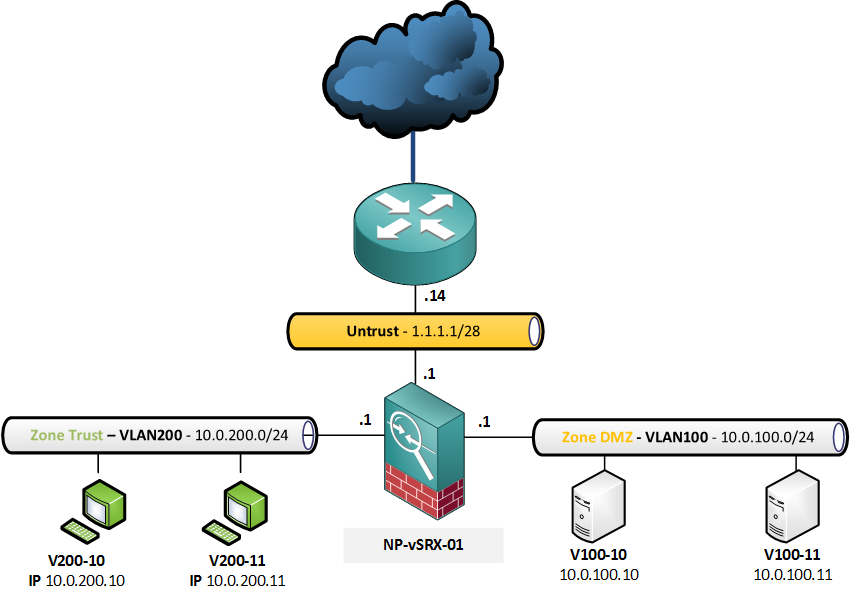
The following Static NAT entries will be configured:
- Server 10.0.100.10 will be translated to 1.1.1.10
- Server 10.0.100.11 will be translated to 1.1.1.11
Using the Global Address Book
Instead of using regular IP prefixes as matching conditions, I will be using address book entries in the NAT config. Referring to the same names in both security policy and NAT makes interpreting and troubleshooting the config much more straightforward.
First, navigate over to the global address book under Security, and enter addresses as you would under the zones. I am creating objects for both the public and private addresses:
[edit security address-book global] root@NP-vSRX-01# show address Host-Private-10.0.100.10 10.0.100.10/32; address Host-Private-10.0.100.11 10.0.100.11/32; address Host-Public-1.1.1.10 1.1.1.10/32; address Host-Public-1.1.1.11 1.1.1.11/32;
Caution, when you start adding entries to the global address book, the SRX will start spawning this error when trying a commit:
[edit security zones security-zone untrust] root@NP-vSRX-01# show ## ## Warning: Zone specific address books are not allowed when there are global address books defined ##
From the looks of it, you will need to move all your zone address books over to the global one, so make sure you start off right on a new SRX. Worst case, you can still match on regular IP prefixes for NAT.
Next will be to define a ruleset, and create some rules. One thing to keep in mind is that you configure the NAT rule to match on the destination address to perform the NAT. Implicitly, the SRX will then create a reverse source-NAT mapping. Just imagine the traffic entering your network, and to what address it should be translated, and the SRX will take care of the reverse traffic for you.
Here is the configuration for the first host, referencing the object name by using destination-address-name:
[edit security nat static]
root@NP-vSRX-01# show
rule-set Static-From-Untrust {
from zone untrust;
rule NAT-DMZ-10 {
match {
destination-address-name Host-Public-1.1.1.10;
}
then {
static-nat {
prefix-name {
Host-Private-10.0.100.10;
}
}
}
}
}
Copy paste for the second host:
rule NAT-DMZ-11 {
match {
destination-address-name Host-Public-1.1.1.11;
}
then {
static-nat {
prefix-name {
Host-Private-10.0.100.11;
}
}
}
}
Verification
The most useful command for Static NAT verification is show security nat static rule, which shows you both a config overview and a hit count.
root@NP-vSRX-01> show security nat static rule all
Total static-nat rules: 2
Total referenced IPv4/IPv6 ip-prefixes: 4/0
Static NAT rule: NAT-DMZ-10 Rule-set: Static-From-Untrust
Rule-Id : 1
Rule position : 1
From zone : untrust
Destination addresses : Host-Public-1.1.1.10
Host addresses : Host-Private-10.0.100.10
Netmask : 32
Host routing-instance : N/A
Translation hits : 40
Successful sessions : 34
Failed sessions : 6
Number of sessions : 0
Static NAT rule: NAT-DMZ-11 Rule-set: Static-From-Untrust
Rule-Id : 2
Rule position : 2
From zone : untrust
Destination addresses : Host-Public-1.1.1.11
Host addresses : Host-Private-10.0.100.11
Netmask : 32
Host routing-instance : N/A
Translation hits : 112
Successful sessions : 112
Failed sessions : 0
Number of sessions : 0
To emphasize that no PAT is performed, here is an output of the session table. We are using port 50973 on both ends of the firewall.
Session ID: 15148, Policy name: FW-PermitWeb/7, Timeout: 4, Valid In: 10.0.100.11/50973 --> 91.189.92.200/80;tcp, If: ge-0/0/1.0, Pkts: 26, Bytes: 5673 Out: 91.189.92.200/80 --> 1.1.1.11/50973;tcp, If: ge-0/0/0.0, Pkts: 25, Bytes: 5863
Thanks for your blog, its helpful.
A simple question though, what security policy you would use for the dmz servers ? i mean between untrust and dmz ? can you write those as well pls ?
Hi Emad
I no longer have the topology running, but I believe it had the same security policy for untrust>dmz applied as in this post
Thanks for reading!
Simon