In this lab, we will look at configuring the SRX to translate the destination field for incoming traffic, which is widely used for public servers in a DMZ.
As with all the NAT examples, I’ll be using the following topology:
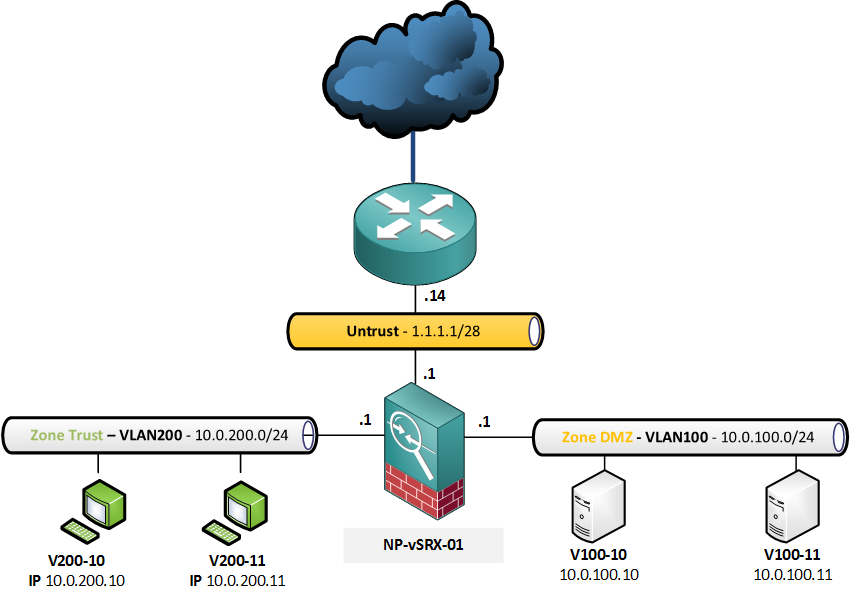
These are the requirements for the translations:
- Only applies to traffic coming from the internet (untrust zone)
- Destination 1.1.1.10/32 will be translated to DMZ IP 10.0.100.10/32
- Destination 1.1.1.11/32 will be translated to DMZ IP 10.0.100.11/32
First, I will configure security policies for the following services:
- Server 10.0.100.10 is hosting a Telnet server
- Server 10.0.100.11 is an SSH/SFTP server
Because DNAT happens before policy lookup, we always refer to the address as it will be after translation.
[edit security policies from-zone untrust to-zone dmz]
root@NP-vSRX-01# show
policy FW-Telnet-Server {
match {
source-address any;
destination-address Host-10.0.100.10-32;
application junos-telnet;
}
then {
permit;
log {
session-close;
}
}
}
policy FW-SSH-Server {
match {
source-address any;
destination-address Host-10.0.100.11-32;
application junos-ssh;
}
then {
permit;
log {
session-close;
}
}
}
As this is a fresh config, we will first define a rule-set that specifies the traffic direction. Destination NAT does not give you the option to specify the to-zone, just the source zone.
[edit security nat destination]
root@NP-vSRX-01# show
rule-set DNAT-From-Untrust {
from zone untrust;
}
Now, let’s add the two pools:
[edit security nat destination]
root@NP-vSRX-01# show
pool DNAT-Host100-11 {
address 10.0.100.11/32;
}
pool DNAT-Host100-10 {
address 10.0.100.10/32;
}
And here are the NAT rules themselves:
[edit security nat destination rule-set DNAT-From-Untrust]
rule DNAT-Host100-10 {
match {
destination-address 1.1.1.10/32;
}
then {
destination-nat {
pool {
DNAT-Host100-10;
}
}
}
}
rule DNAT-Host100-11 {
match {
destination-address 1.1.1.11/32;
}
then {
destination-nat {
pool {
DNAT-Host100-11;
}
}
}
}
Because the upstream router is in the same segment as our firewall, we will also need to add ProxyARP to the global NAT config.
[edit security nat] root@NP-vSRX-01# set proxy-arp interface ge-0/0/0.0 address 1.1.1.10/32 to 1.1.1.11/32
Verification
After starting a telnet and SSH session from my PC, this is the session table:
Session ID: 166748, Policy name: FW-SSH-Server/6, Timeout: 1792, Valid In: 10.6.66.68/59016 --> 1.1.1.11/22;tcp, If: ge-0/0/0.0, Pkts: 3, Bytes: 132 Out: 10.0.100.11/22 --> 10.6.66.68/59016;tcp, If: ge-0/0/1.0, Pkts: 2, Bytes: 126
Session ID: 166759, Policy name: FW-Telnet-Server/5, Timeout: 1798, Valid In: 10.6.66.68/60731 --> 1.1.1.10/23;tcp, If: ge-0/0/0.0, Pkts: 11, Bytes: 510 Out: 10.0.100.10/23 --> 10.6.66.68/60731;tcp, If: ge-0/0/1.0, Pkts: 14, Bytes: 652
root@NP-vSRX-01> show security nat destination summary
Total pools: 2
Pool name Address Routing Port Total
Range Instance Address
DNAT-Host100-11 10.0.100.11 - 10.0.100.11 0 1
DNAT-Host100-10 10.0.100.10 - 10.0.100.10 0 1
Total rules: 2
Rule name Rule set From Action
DNAT-Host100-11 DNAT-From-Untrust untrust DNAT-Host100-11
DNAT-Host100-10 DNAT-From-Untrust untrust DNAT-Host100-10
root@NP-vSRX-01> show security nat destination pool all
Total destination-nat pools: 2
Pool name : DNAT-Host100-11
Pool id : 3
Total address : 1
Translation hits: 1
Address range Port
10.0.100.11 - 10.0.100.11 0
Pool name : DNAT-Host100-10
Pool id : 4
Total address : 1
Translation hits: 8
Address range Port
10.0.100.10 - 10.0.100.10 0
Hi Dear
I do your configur step by step and I NAT Destination 1.1.1.10/32 will be translated to DMZ IP 10.0.100.10/32 for HTTP protocol.
But I have a problem Why I can ” telnet 10.0.100.10 80 ” from client in untrust zone ??
Sorry for the late response, this comment slipped under the radar.
I suppose you are routing the 10 network to the untrust interface then? In real life, the private addresses wouldn’t be routed to the external interface.
You can add the following to your security policy:
set policy then permit destination-address drop-untranslated
This will drop traffic that was not NAT’ed: https://www.juniper.net/documentation/en_US/junos/topics/reference/configuration-statement/security-edit-destination-address-security-policy-flag.html