A common technique to obscure services from network probing is to host them on ports outside of the well-known ports range. This might help as a first defense, but in reality the ports are still there for anyone who steps out of the defaults. It also makes life harder for other firewall engineers 🙂 On the other hand, if your ISP is blocking services hosted in the well-known range, it might be your only option.
As in all the NAT examples, here is the topology:
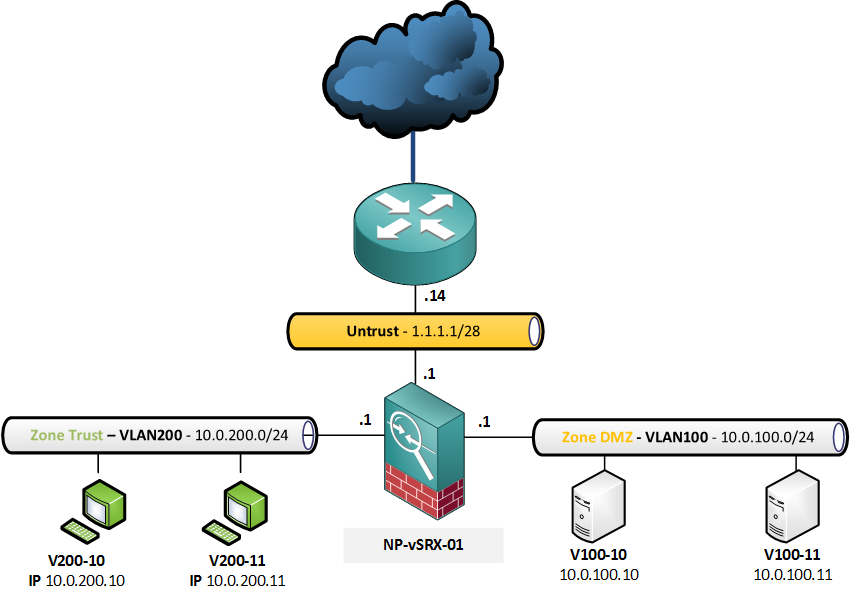
We are hosting an SFTP server, but are fed up with all the bruteforce attacks, so decide to host it on a different port. Traffic coming from the untrust zone, destined for 1.1.1.11 and arriving at TCP port 2222, will be translated to port 22 on the inside.
First, we define the real, internal port at the DNAT pool, together with the internal IP.
[edit security nat destination] root@NP-vSRX-01# show pool DNAT-Host100-11 address 10.0.100.11/32 port 22;
Then, we go to our rule set, which defined the traffic direction (from untrust) and enter the address and port on which it should be listening, plus the pool to translate to:
[edit security nat destination rule-set DNAT-From-Untrust]
root@NP-vSRX-01# show
from zone untrust;
rule DNAT-Host100-11 {
match {
destination-address 1.1.1.11/32;
destination-port {
2222;
}
}
then {
destination-nat {
pool {
DNAT-Host100-11;
}
}
}
}
That’s it. After doing a telnet to port 2222, we see the following flow in the table:
Session ID: 167059, Policy name: FW-SSH-Server/6, Timeout: 1778, Valid In: 10.6.60.68/62340 --> 1.1.1.11/2222;tcp, If: ge-0/0/0.0, Pkts: 3, Bytes: 132 Out: 10.0.100.11/22 --> 10.6.60.68/62340;tcp, If: ge-0/0/1.0, Pkts: 2, Bytes: 126
Port forwarding with a dynamic IP
If you are running a dynamic IP address, it won’t be possible to define one IP as a match condition. Unless your ISP is always handing out addresses in one specific range, the only option is to define the destination-address as 0.0.0.0/0
All config stays the same, but the DNAT rule looks like this:
[edit security nat destination rule-set DNAT-From-Untrust rule DNAT-Host100-11]
root@NP-vSRX-01# show
match {
destination-address 0.0.0.0/0;
destination-port {
2222;
}
}
then {
destination-nat {
pool {
DNAT-Host100-11;
}
}
}